First-Order Automated Reasoning with Theories: When Deduction Modulo Theory Meets Practice | SpringerLink
Selected Papers from the 2018 41st International Conference on Telecommunications and Signal Processing (TSP)
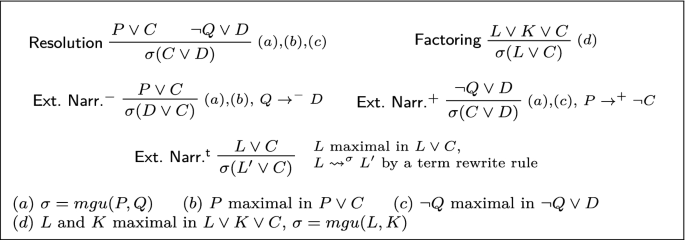
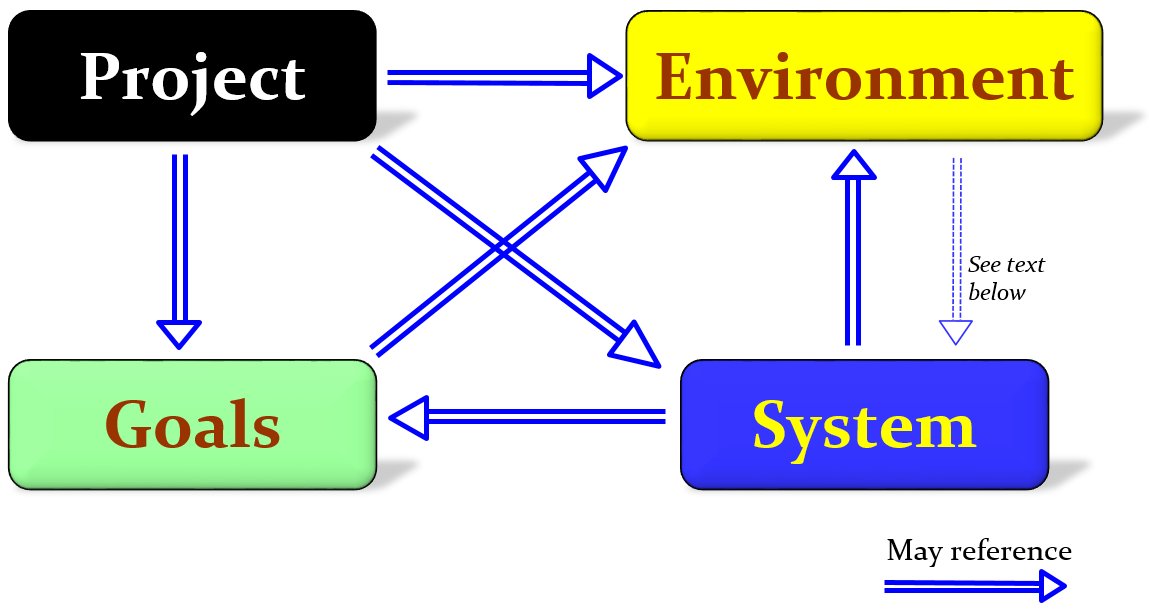
First-Order Automated Reasoning with Theories: When Deduction Modulo Theory Meets Practice | SpringerLink
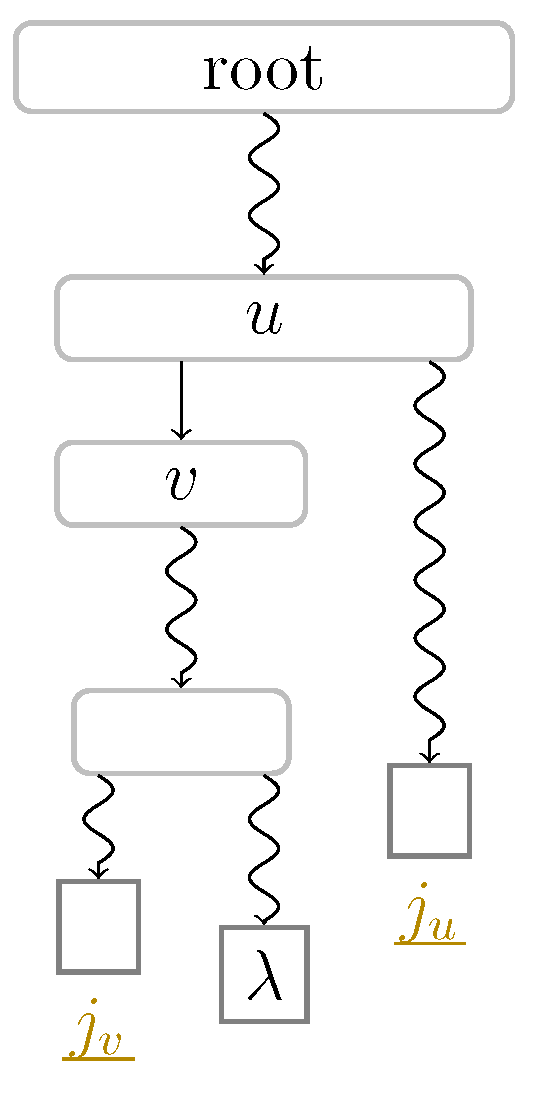
Algorithms | Free Full-Text | Non-Overlapping LZ77 Factorization and LZ78 Substring Compression Queries with Suffix Trees | HTML
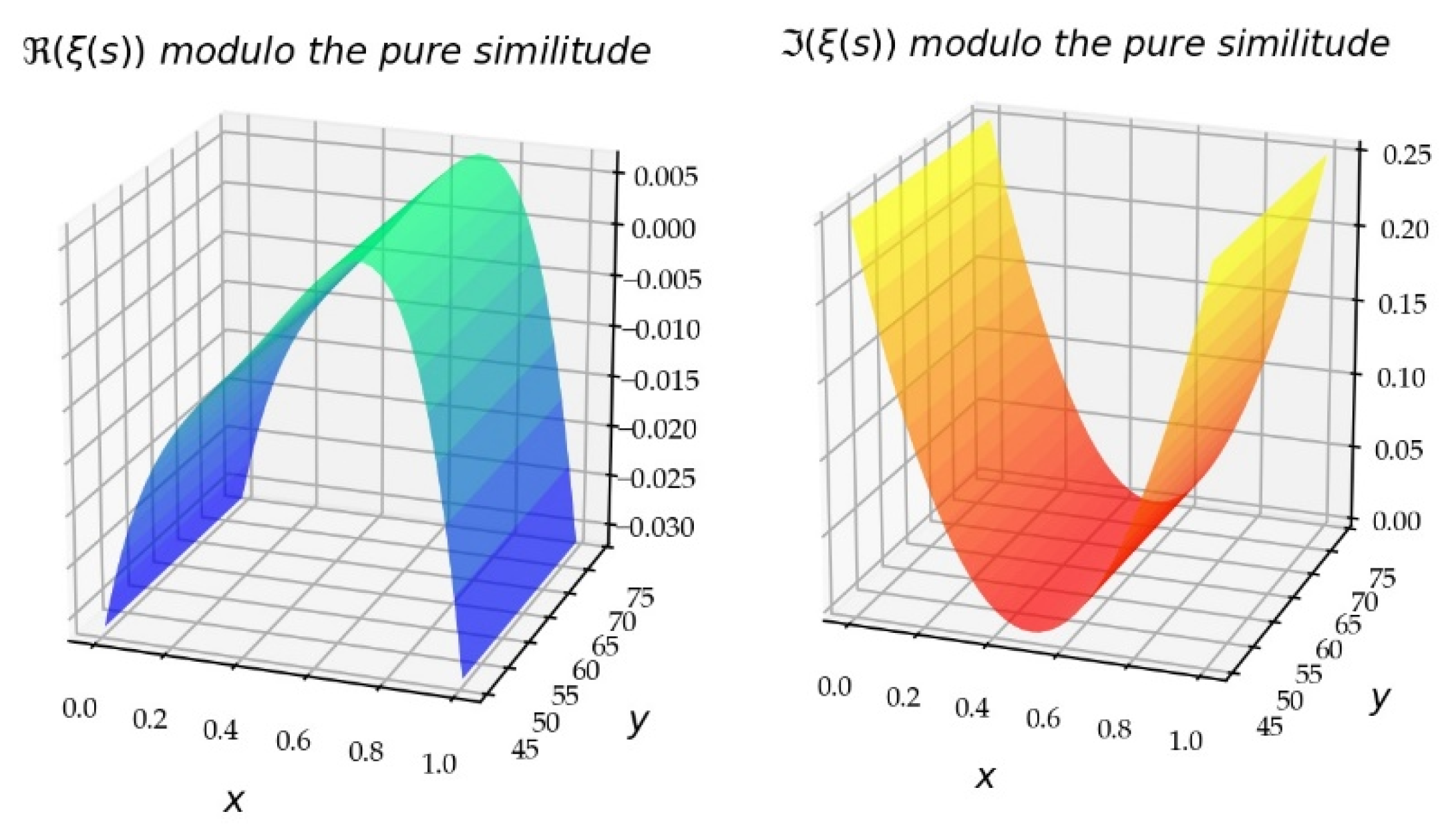
Information | Free Full-Text | Numerical Calculations to Grasp a Mathematical Issue Such as the Riemann Hypothesis | HTML