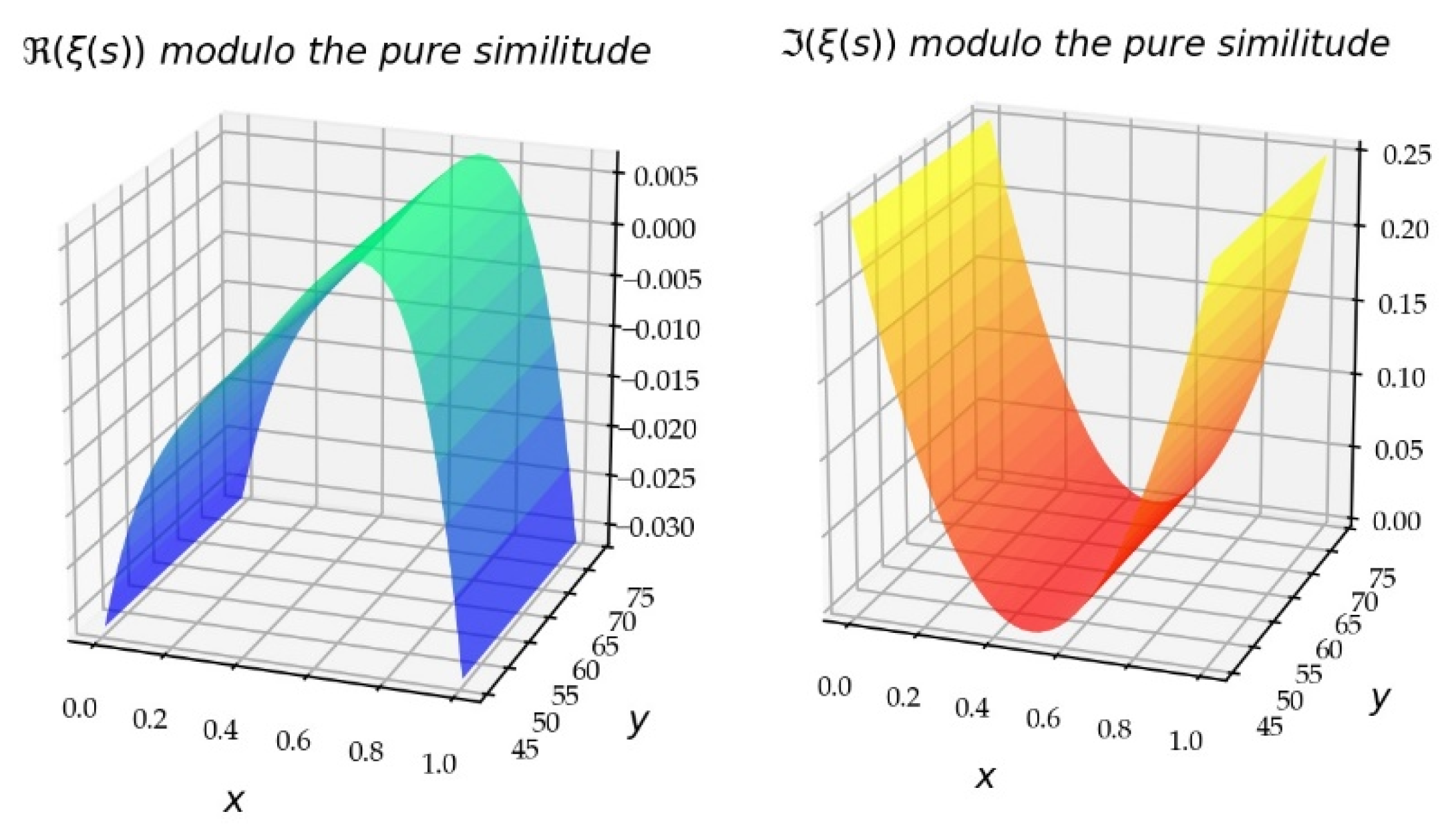
Information | Free Full-Text | Numerical Calculations to Grasp a Mathematical Issue Such as the Riemann Hypothesis | HTML

First-Order Automated Reasoning with Theories: When Deduction Modulo Theory Meets Practice | SpringerLink

On the identification and analysis of Skype traffic - Molnár - 2011 - International Journal of Communication Systems - Wiley Online Library
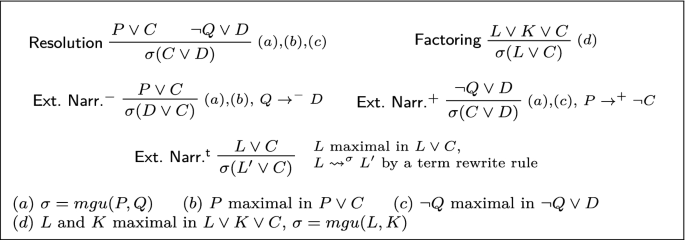
First-Order Automated Reasoning with Theories: When Deduction Modulo Theory Meets Practice | SpringerLink

Post quantum secure conditional privacy preserving authentication for edge based vehicular communication - Dharminder - 2021 - Transactions on Emerging Telecommunications Technologies - Wiley Online Library

Adjustable Foldable Laptop Stand Desk Notebook Stand Portable Laptop Holder Tablet Stand Computer Support|Laptop Stand| - AliExpress